Connections Galore from South Korea
One OpenCanary was subjected to a massive attack in 2024: over 7 million connections from a single Korea Telecom IP (220.120.147.167) targeted an OpenCanary instance located in Switzerland, occurring in four separate, large-scale events.
The fact that the attack was confined to a single IP, a single honeypot, and exclusively port 1433 (TCP) – the open Microsoft SQL Server port – strongly suggests an attempt to access data from a mistakenly exposed MSSQL database.
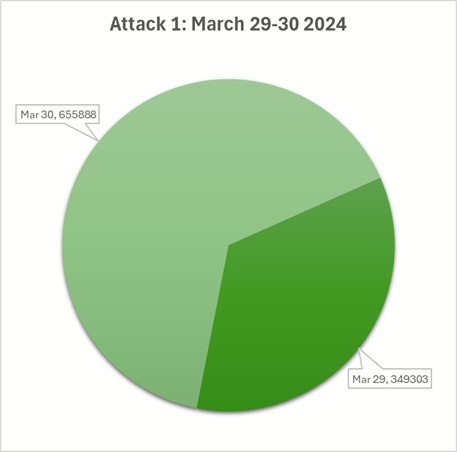
Attack 1: From March 29th to 30th
The first attack was launched, generating a total of 1,005,191 connections against the MSSQL port.
The attack escalated from over 340,000 connections on the 29th to over 650,000 on the 30th, strongly suggesting a persistent attempt to compromise the database.
The attack rate over the 2 days was around 500’000 attempts per day.
The attacks then disappeared for 67 days.
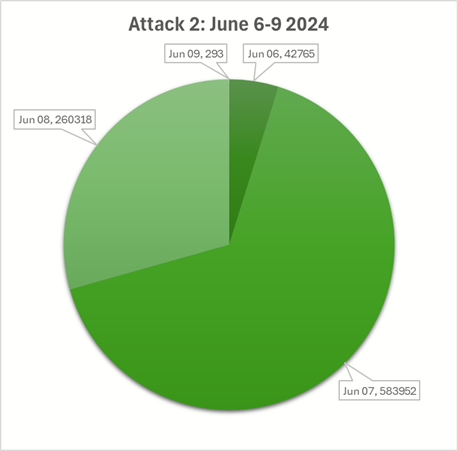
Attack 2: From June 6th to June 9th
There was a second attack. The attack started late on June 6th and stopped early on June 9th – so was effective over approximately 3 days.
The average daily connection rate was lower, at around 300’000 attempts per day which may reflect attempts to slow the attack and understand what the responses were from the server.
Perhaps at this time, the hacker was frustrated as he (or she) was not seen for a further 73 days.
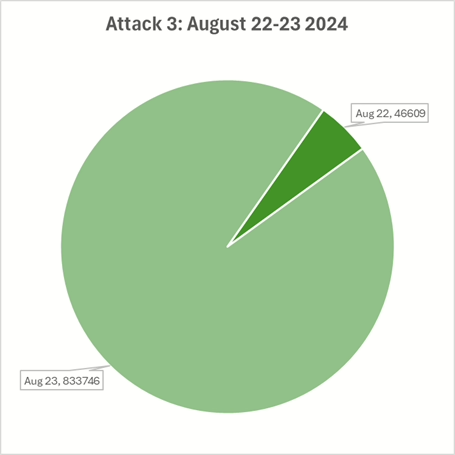
Attack 3: August 22nd to 23rd
The next attack started late on August 22nd with around 50’000 attempts to gain access to data; August 23rd saw the connection rate increase beyond 800’000 attempts – which appears to be the peak that the attacker could sustain.
And still no access to any data. Mostly because there is no data there to access….
The attacker disappeared for 72 days.
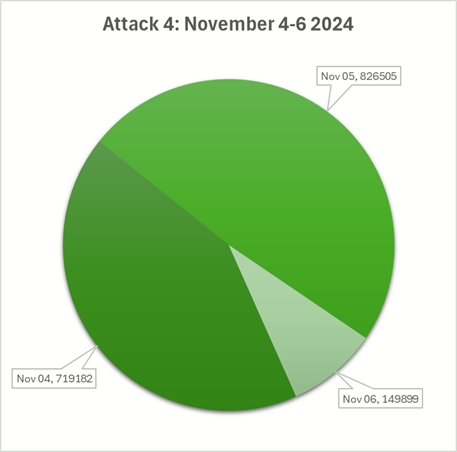
Attack 4: November 4th to 6th
The attacker returned on November 4th, late in the day. Over around 55 hours, there were over 1.6 million connections with the peak running across 2 days of 800’000 connections per day (over 550 per second!).
Probably frustrated, the connections stopped for 24 days.
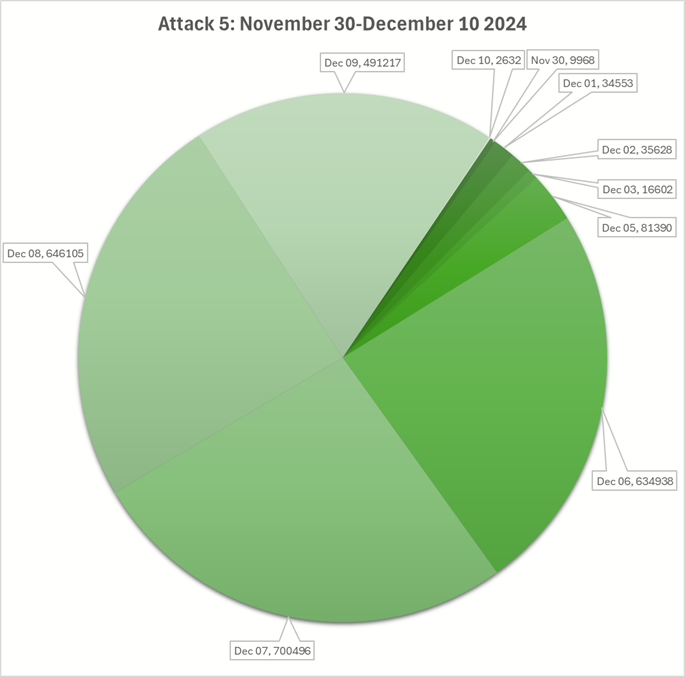
Attack 5: Bigger, Better? Certainly Longer.
From November 30th until December 3rd, there were under 100’000 connections which may suggest the attacker was crafting and adapting the script to try to brute force access to the MSSQL data.
It could be that the script was adapted on December 4th as there were no connections……they began again on December 5th.
Starting late on the 5th and finishing in the early hours of the 10th, there were 2.5 million connections, still attempting to steal data.
Sadly, there was still no data there to steal….
Conclusion and Assumptions
The attacker likely discovered the exposed MSSQL port either through targeted scanning or, more plausibly, by leveraging a publicly available list of vulnerable systems. Their repeated focus on this MSSQL server suggests they believe it contains valuable data worth exploiting.
The persistent nature of the attacks—occurring across five distinct time intervals—implies the attacker may be an individual using basic tools rather than an automated or highly sophisticated threat actor. Notably, this single attacker accounted for 38% of all MSSQL connection attempts across monitored honeypots in 2024, indicating unusually high and sustained interest.
While the open port did not yield the attacker any success, their repeated efforts suggest a significant investment of time—potentially diverting attention from other, more vulnerable targets. In this case, the honeypot may have served as an effective decoy, wasting the attacker’s resources and possibly preventing breaches elsewhere.



